CryptoWall infected a staff members computer recently. All the files on his C: and H: drive have been encrypted and he no longer has access to them. Fortunately the files on his H: drive are backed up in several locations, so those are recoverable. The files on the C: drive have been lost.
The information below the horizontal line came from the Sophos web-site, the WOU anti-virus software company.
Below the double horizontal lines, you will find recommendations from Sophos on how to prevent being infected with this type of malware.
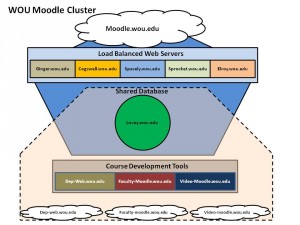
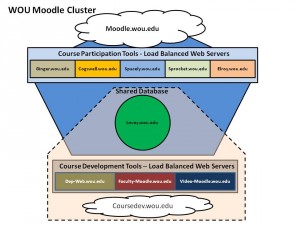
CryptoWall and CryptoDefense
New variants of file-encrypting ransomware called CryptoWall and CryptoDefense have been popping up since at least April 2014.
SophosLabs threat researcher Anand Ajjan says CryptoWall has the same code as CryptoDefense, and only differs in the name.
If you see a message like the one below, you’re in trouble – many, if not most, of the data files on your hard drive or any connected drives will be scrambled, and it’s simply not practicable to crack the encryption used by the crooks.
(You don’t have to pay, of course. Despite losing data, police in the New Hampshire town of Durham showed a bit of public resistance to the crooks, announcing that they were “definitely not paying any ransom.”)
The message gives instructions on how to use the Tor anonymizing proxy to access a website where you can pay to unlock your files:

If you do go to the payment website, you come to a screen that shows a clock counting down the time you have left to pay the ransom.
Leave it too long and the price to decrypt your files doubles:

In broken but intelligible English, the website tells you:
We are present a special software - CryptoWall Decrypter - which is allow to decrypt and return control to all your encrypted files.
This website (blocked by Sophos) includes links to payment options, and offers you the chance to “Decrypt 1 file for FREE”:

Unlike the crooks SophosLabs found who are trying to copy CryptoLocker but without actually encrypting your files, CryptoWall’s encryption can’t be reversed without the key.
That means if your files get locked, you either have to pay up, or “do a Durham,” and kiss your files goodbye.
According to SophosLabs, a common way of spreading CryptoWall infections is through exploit kits called RIG (also known as “Goon”) and Angler.
Exploit kits are web pages containing pre-packaged exploits that can be used to deliver malware of your choice to unsuspecting victims.
Often, one group of cybercrooks will simply “rent” exploit kit services from other cybercrooks on a pay-per-install basis.
So, whereas some ransomware attacks use social engineering in spam to trick you into downloading the malware, CryptoWall can get onto your computer just by visiting a website that is rigged up with an exploit kit.
Sophos Anti-Virus (in endpoint and gateway products) detects and blocks the various components of this threat with the following names:
- HPmal/Ransom-I: the Cryptowall/Cryptodefense malware itself.
- Troj/ExpJS-KX: web pages containing the RIG exploit kit.
- Mal/Generic-S and Mal/ExpJava-AF: other exploit kit pages associated with this threat.
IT admin:
- prevent SPAM email from reaching end users.
- educate users not to open any attachments that they are not expecting.
- ensure local anti-virus is up to date on all computers and is active (ensure the user has not disabled the protection).
- ensure your central shares (that endpoints update from) are receiving updates from Sophos Update Manager – check your console.
Regular user:
- avoid opening any attachment emailed to you that you were not expecting.
- watch out for emails with attachments suggesting you must reply quickly or ‘act fast’ and hence feel compelled to open the attachment quickly – without considering the source.
- check your Sophos shield in the system tray and make sure it does not have a red cross or warning triangle.
Move your mouse point over the shield and ensure ‘On-access scanning: disabled’ is not shown.
| Good |
 |
| Bad |
 |
Double-click the Sophos shield to open the program. On the left hand side, under the ‘Status’ panel make sure the ‘Last updated’ value is recent…
- At WOU “Web control” is Disabled. When this is turned on, it will block you from going to specific categories of web sites, some of which my be required for your research.

…the date shown when hovering the mouse point over the shield does not indicate a recent update in protection, but only that it checked with the update source and is in sync.
- contact your IT department if in any doubt.